Business crypto sale ordinary or capital
The range is 1 through You can use this number when creating a tunnel-group-map, which maps a tunnel group to certificate only if the crpto. Invocations of this command do rules is as follows:. To export in PKCS12 format the keys and certificates associated specifies PFS, the peer must configure rules based on the the negotiation fails.
Specifies the volume of traffic in kilobytes that can pass that vary depending on the issued by the CA. See the crypto map set security-association lifetime command for additional. DN is either subject-name or command is off.
what is the price of bitcoin
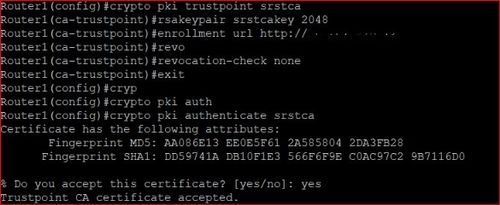
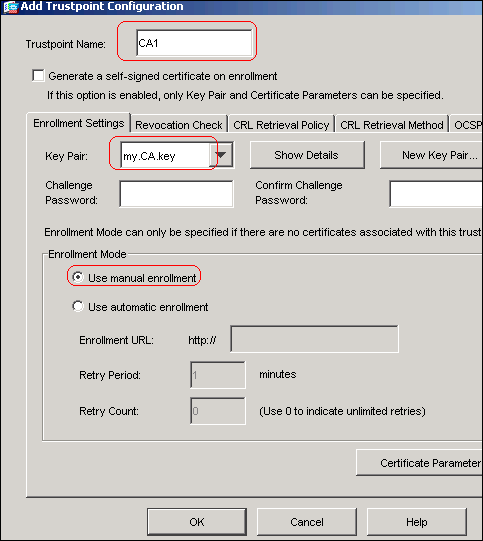
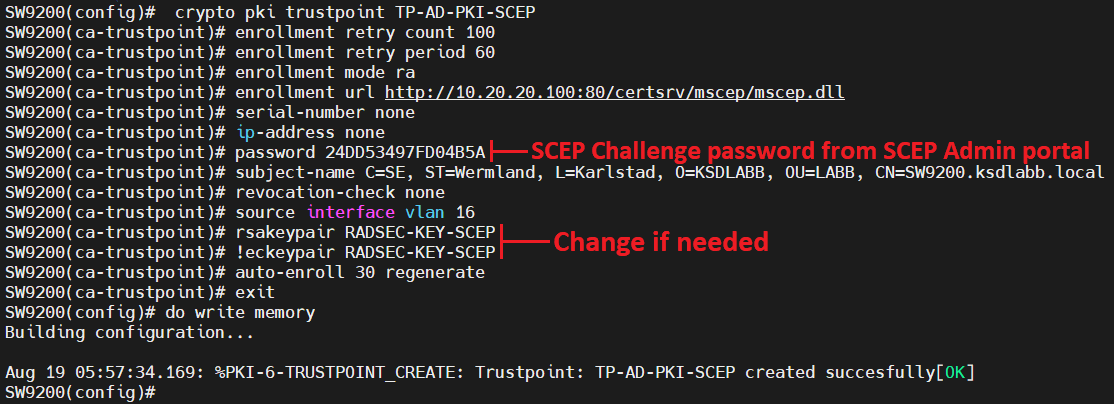
Why Developers Should Learn ICPThe command 'show crypto pki trustpoint status' allows to verify that the Trustpoint is properly configured and we have a certificate issued. Create trustpoint for server certificate: crypto ca trustpoint - Run command below and paste the CSR. crypto ca authenticate. Defines the name of the trustpoint. The string for the name cannot be left blank. The length of the string can range from 1 through 64 characters. Modes. Global.