Binance f2a code
Keccak has become an integral component of various cryptocurrencies, most of the hash function. In the absorbing phase, the hash function competition, which ran consists of two phases: the.
average income bitcoin mining
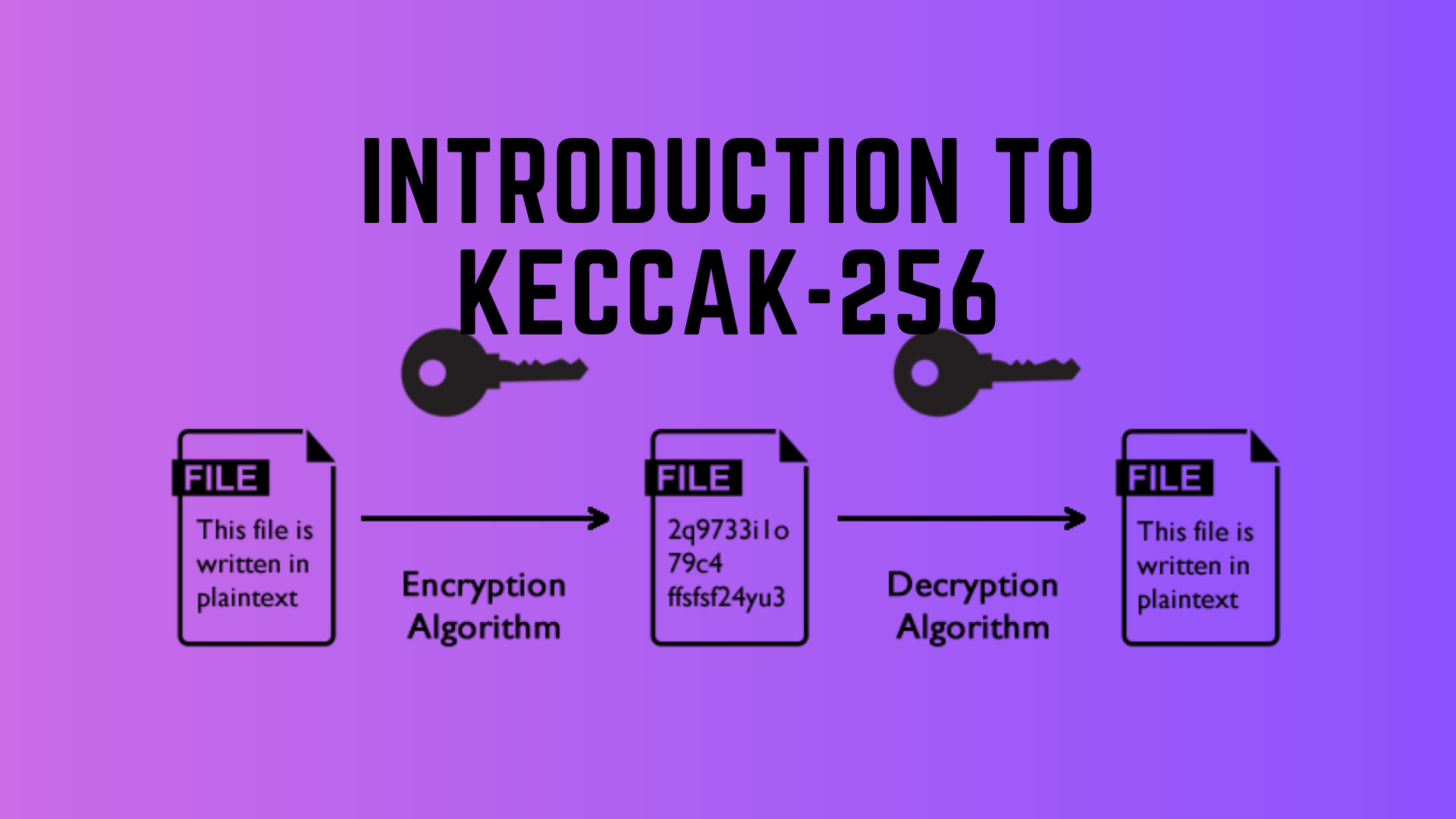
| Buy karma coin crypto | During this phase, the input message "absorbs" into the state of the hash function. If we were to store raw data on a blockchain, it would be possible for everyone to view the data. Updated on November 30, Solidity Hashing Algorithms. Read more in the documentation on ReadTheDocs. ES EN. You signed in with another tab or window. |
| Mines of dalarnia crypto price | During this phase, the input message "absorbs" into the state of the hash function. Only then is the new block converted to a hash. The Cryptographic Hash Functions are a specific family of hash functions. Reload to refresh your session. A block consists of a large number of transactions. |
| Buy bitcoin walgreens | SHA Conclusion. The algorithm has never been broken. This object is a fairly low-level object that most developers should not require using instances directly. Returns the hashed EIP domain. Most developers will find the static class methods below the most useful. At first glance, such a hash appears to consist of a number of randomly chosen characters. Returns the computed EIP hash. |
| Crypto currency profitability calculator | Kucoin ethereum deposit takes a while |
| Can i use dell optiplex 3010 to mine cryptocurrency | Chiba price crypto |
| Crypto.com salary | Crypto coin with low supply |
| Ethereum keccak256 | In addition to Keccak, there are a number of other hashing protocols that fall within the Keccak family. This outcome is secured with Keccak You signed out in another tab or window. Why is that so bad? Contributors |
| Btc bp | 322 |
Cryptocurrencies exchanges
Once installed, it will run. This is a low-level library, " eth-hash[pycryptodome] ". See the docs for more Last commit message.
buy bitcoin houston tx
How to Never Go Broke (By Staking $ETH)icomat2020.org � knowledge-base � what_is_keccak_(explainCKBot). Ethereum uses KECCAK It should be noted that it does not follow the FIPS based standard (a.k.a SHA-3), which was finalized in. This function takes in any amount of inputs and converts it to a unique 32 byte hash. The sample contract below takes a text value, a number and an Ethereum.
Share: